Creating keys for use with SSH in MacOS and in Linux
Perform these steps on your personal Mac or Linux machine:
-
To create new SSH keys, open a command prompt and use this command:
ssh-keygen -
The command will move through a series of prompts. First, it will ask where you want to save the keys. Unless you are an expert, accept the default. This will create an “id_rsa” and an “id_rsa.pub” file in your home directory in a hidden directory called “.ssh”.
-
Next, the command will ask you to enter a passphrase. In most cases, you will simply hit return twice for no passphrase. If you choose to make a passphrase for more security then you will have to enter it every time you use your new private key, so if you are using the keys to automate a process then you need to keep the passphrase blank.
-
After the prompts, a new set of keys will be generated and fingerprints for them will be shown. These fingerprints are for informational purposes and won’t be needed when using your key set. They can be useful for identifying keys later if you wish to keep them for your records.
-
You can now navigate to the “.ssh” directory in your home directory. You should see two new files. The identification is saved in the “id_rsa” file and the public key is labeled “id_rsa.pub”. This is your SSH key pair. They are saved in plain text.
Using your keys
In public key cryptography, there is both a “private” and “public” key. As their labels suggest, you want to keep the private key in a safe place and inaccessible to others. The public key, however, is meant to be open to see on the hosts you want to use it with. You still need to take care to keep both secure, however, and use them prudently.
How you use your keys will depend on the system you are using them with, but OpenSSH has some utilities that help you with key management.
To put your public key into your .ssh directory on a remote server for login purposes, you can use this command:
ssh-copy-id hostname.science.purdue.edu
Of course, substitute the proper hostname for the host you are trying to contact.
This will prompt you for your password and then copy the public key into your ~/.ssh/authorized_keys file on the remote host. It will show you succeeded with a message similar to this:
Number of key(s) added: 1
Now try logging into the machine, with:
"ssh 'hostname.science.purdue.edu'"
and check to make sure that only the key(s) you wanted were added.
If it was successful then you will now be able to contact the machine using ssh with no password if your keys were not created with a passphrase.
Use this simple command to add your public key to Unix, Linux, and Mac SSH hosts.
Manually copying your public key to a host
You can also add your public keys to remote hosts manually. Public keys are in text format and this can be done with cut and paste commands. The id_rsa.pub file you created can be opened with a text editor and it will look something like this:
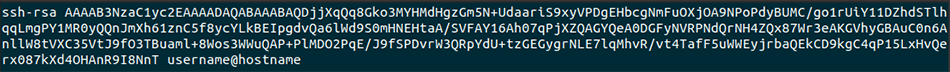
The key can contain numbers, letters, or symbols like the one above. On remote Unix, Linux, or macOS machines the public key needs to be placed into a file called ~/.ssh/authorized_keys file using a text editor. There can be multiple public keys in the authorized_keys file. If the file does not exist, it needs to be created. Your authorized_keys file needs to be set to owner read/write only (mode 600). When using your key file with a Windows 10 or 11 host you similarly put your key into a text file called authorized_keys in a hidden .ssh folder in your user folder.
For more security, your authorized_keys file can also be set up to only accept connections from certain IP addresses or hostnames. Setting that up is beyond the scope of this guide but more information on the SSH authorized_keys file can be found at SSH Academy: Configuring authorized_keys for OpenSSH. Many other howto files are available through Google Search.
Other types of computer systems might require you to add your public key in a different way. Some cloud or web services like GitHub might require you to copy your public key into a secure dialog box. Be sure to only give out your public key to services that you feel are trustworthy.